The adventures of super(er) google admin: reduce your attack surface for free!

Hello, Super Admin
If any of your Google Workspace Super Admin accounts are compromised, it can lead to the loss of your Google Workspace. You know that, right? So you are protecting these accounts with extra care. Aren’t you? And you have at least two accounts with Super Admin Privileges, don’t you? And all your Super Admins have two accounts – a Super Admin account that they use only for managing your Workspace, and a regular account for day-to-day work, right? And the Super Admin accounts don’t have access to any services but the necessary ones, right? And you’re not paying for two accounts for your Super Admins, aren’t you? Because you know about Google Cloud Identify, don’t you?No? Then welcome to the VMGWU – the Vast Majority of Google Workspace Users.Google Workspace Super Admin accounts are treated differently than ordinary accounts. They have complete access to everything: managing users, security, billing, access to all data, assigning privileges, including the ability to give other people other Super Admin privileges. Because Super Admin accounts are, well, “super,” it’s easy to fall into a configuration trap where they don’t follow the security policies you set for other accounts; This Can Be Bad(™) because If you are not careful, Super Admin accounts can have weaker security than other accounts.Thankfully, from the moment you signed up, across the countless settings and internal products, Google guided you unerringly to best security practices. Didn’t they? Didn’t think so.Ok, let’s get real: If you are a founder, you started by using a Super Admin account, you are still using it and odds are you will be until you finish reading this article. How do I know the odds? Because that’s the default UX!Here’s how it works. Right after you bought your domain name, you went to set up Google Workspace. You then proved ownership of the domain and gave Google your credit card and Google sent an email to their email address and made them the account admin with Super Admin privileges. Google Workspace is a powerful and complex product and setting it up properly is important to make it secure. That’s why everyone starts by spending two days on the FREE “Introduction to Google Workspace” course watching the 16 videos and reading the 22 documents then two more days on the FREE Managing Google Workspace course watching 14 videos and reading 30 documents, and then the FREE “Google Workspace Security” with 9 more videos and 14 more documents. Congratulations on your first day as CISO!Haha. Nobody does that. Unless you are the CISO. What pretty much everyone does is what we did: live in blissful ignorance until something bad happens, like a breach of SOC2 compliance. So we went through the obvious steps to set things up and searched the Workspace Docs, checked StackOverflow, and asked ChatGPT when we had a problem. Though, to be fair, we got slightly carried away, obsessed even, and decided to build a company to solve this, and other related problems.So, because that first account was, by default, a super-admin account, and because of the friction involved in fixing it, it’s most probably the account you’re still using.Let me save you a few weeks, some money, and help you get back to work.Don’t use a super admin account for daily activitiesGoogle has a handy checklist Security best practices for administrator accounts - Google Workspace Admin Help that everyone who doesn’t do the courses knows about because it’s a needle in the vast haystack of Google Workspace documentation.The first two bullets are about multi-factor authentication. Now, before you go running to talk to your SSO solutions vendor, you should know one of the ways that Super Admin accounts are treated differently is that they are excluded from third-party security solutions, and that’s a good thing that could’ve been communicated better.

Ok, so the recommendation is “Don’t use a super admin account for daily activities.” Why? “If one account is lost or compromised, another super admin can perform critical tasks while the other account is recovered.” That makes perfect sense with everything we know and how targeted Super Admin accounts are! And so does the recommendation above it, “Set up multiple super admin accounts.”There are two ways to do this. There’s a pretty-easy-way-that-costs-money, the complex-way-that-is-free-and-more-secure, and - coming soon - a third way: The YeshID semi-automated way; subscribe!
Pay up
The simple way is to create another admin account per admin user:
- admin-maria@example.com, maria@example.com
- admin-james@example.com, james@example.com
Then you set each “admin-” account as a super admin, login as super admin and remove super admin privileges from your normal account. Done!If you’re like most small businesses that follow Google’s recommendation you probably have one Super Admin for each of the founders and one custom admin for the engineering lead. OK, maybe not custom roles, but more on that another time. It would have cost us only a couple of extra hundred a year and more as the organization grew, plus you need to remember to check those admin email boxes for important messages. Not great.
More secure and free!
Because super admin accounts are so valuable, it is best to limit the attack surface as much as possible. I like disabling all services associated with a super admin account, such as Google Drive and email. If we disable all the services, we might as well not pay for the unused services! Here’s how:
- Add a Google Identity Free. Go to admin.google.com > Billing > Subscriptions, and add a “Cloud Identity Free” subscription.
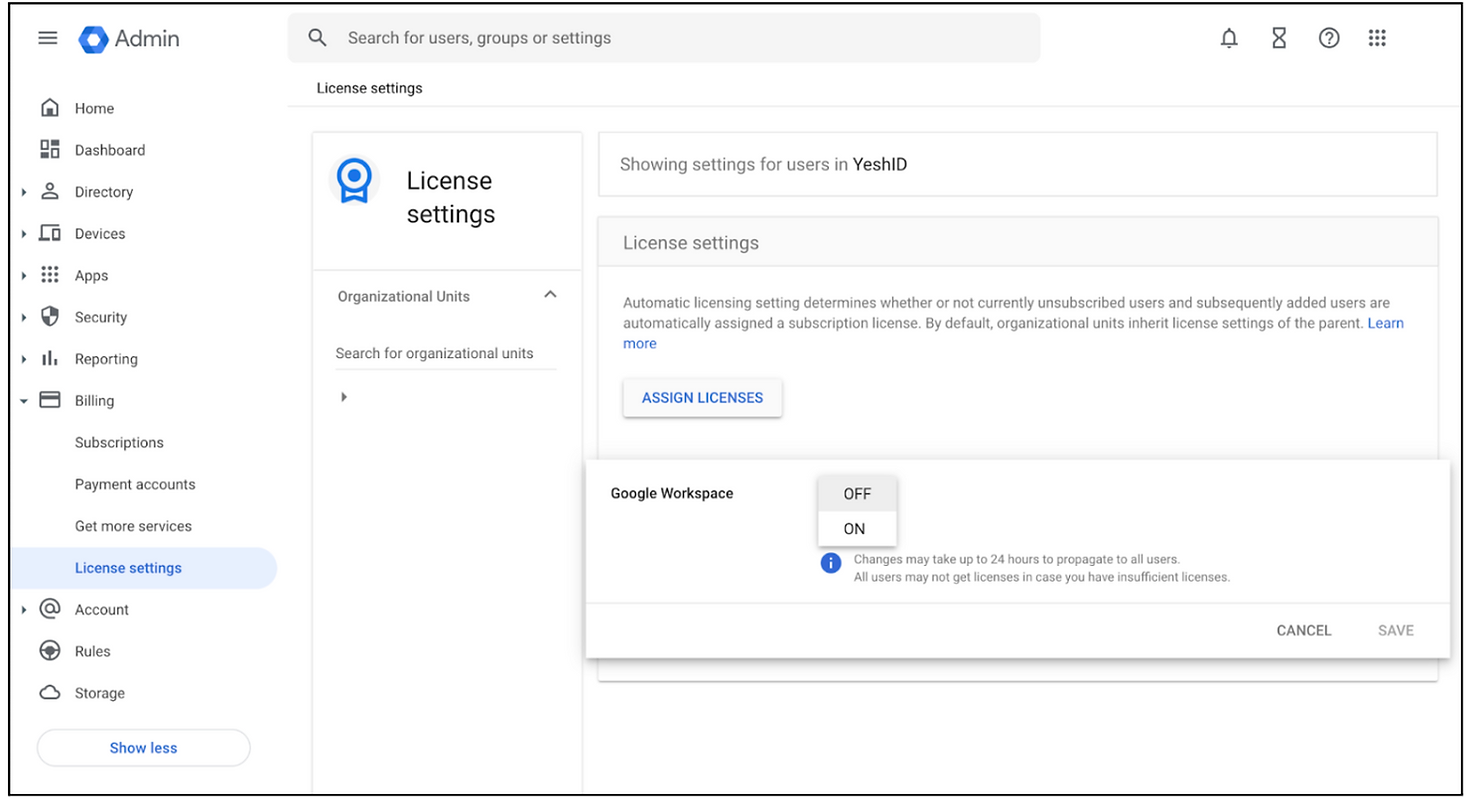
- Turn off automatic Google Workspace licensing during setup. Go to admin.google.com > Billing > License settings. Press “Automatic licensing” on the right, and change to OFF.
- Create a new account and give it super admin access. Make sure it has a strong password and MFA activated.
- Validate the account is using only Cloud Identity Free license
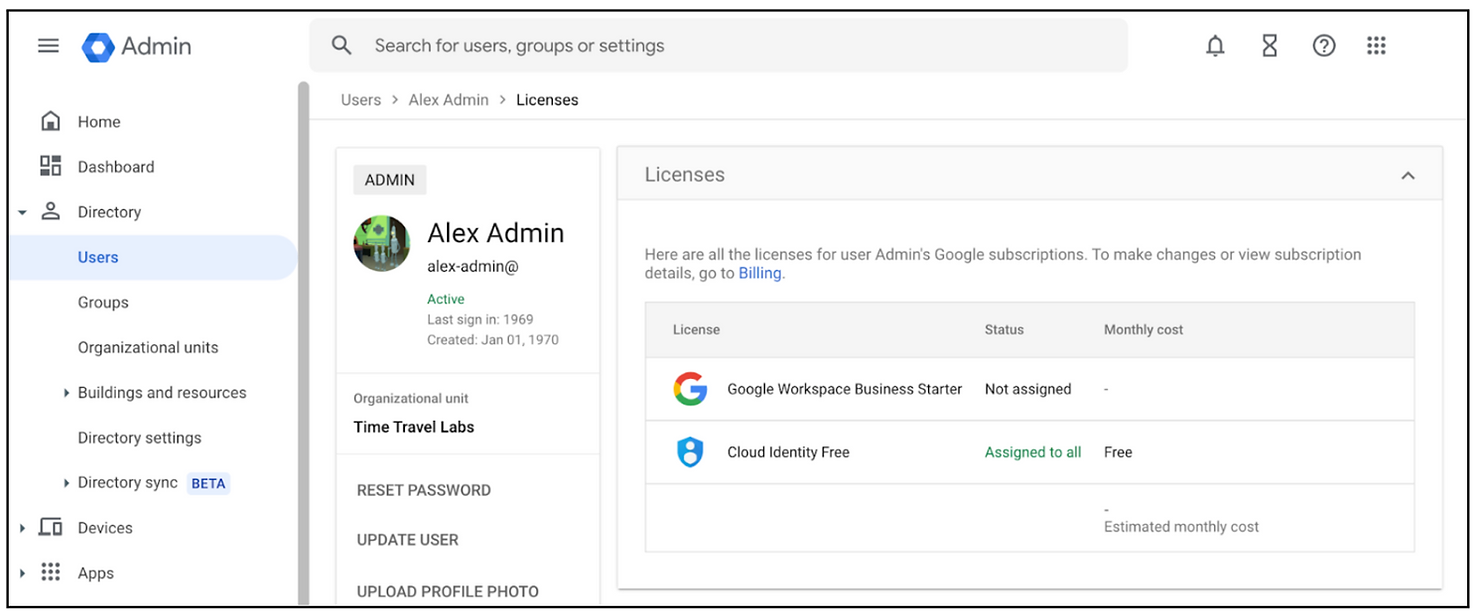
- Ok, now you have a super admin account, that is free, and has no services attached to it.
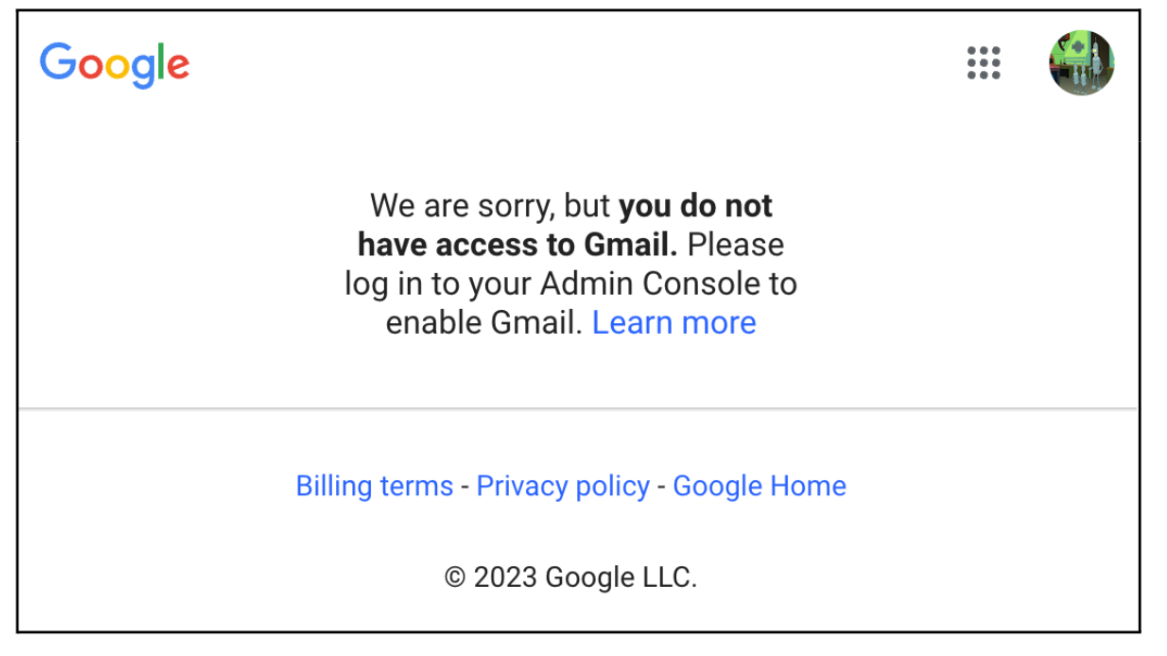
- Super admin accounts get special alerts and notifications. Because this account doesn’t have any, we need to solve it, using routing.
- Add email routing. Go to Apps > Google Workspace > Gmail > Default routing. From there, intercept emails that would be sent to your free Admin account and redirect them to your user account.
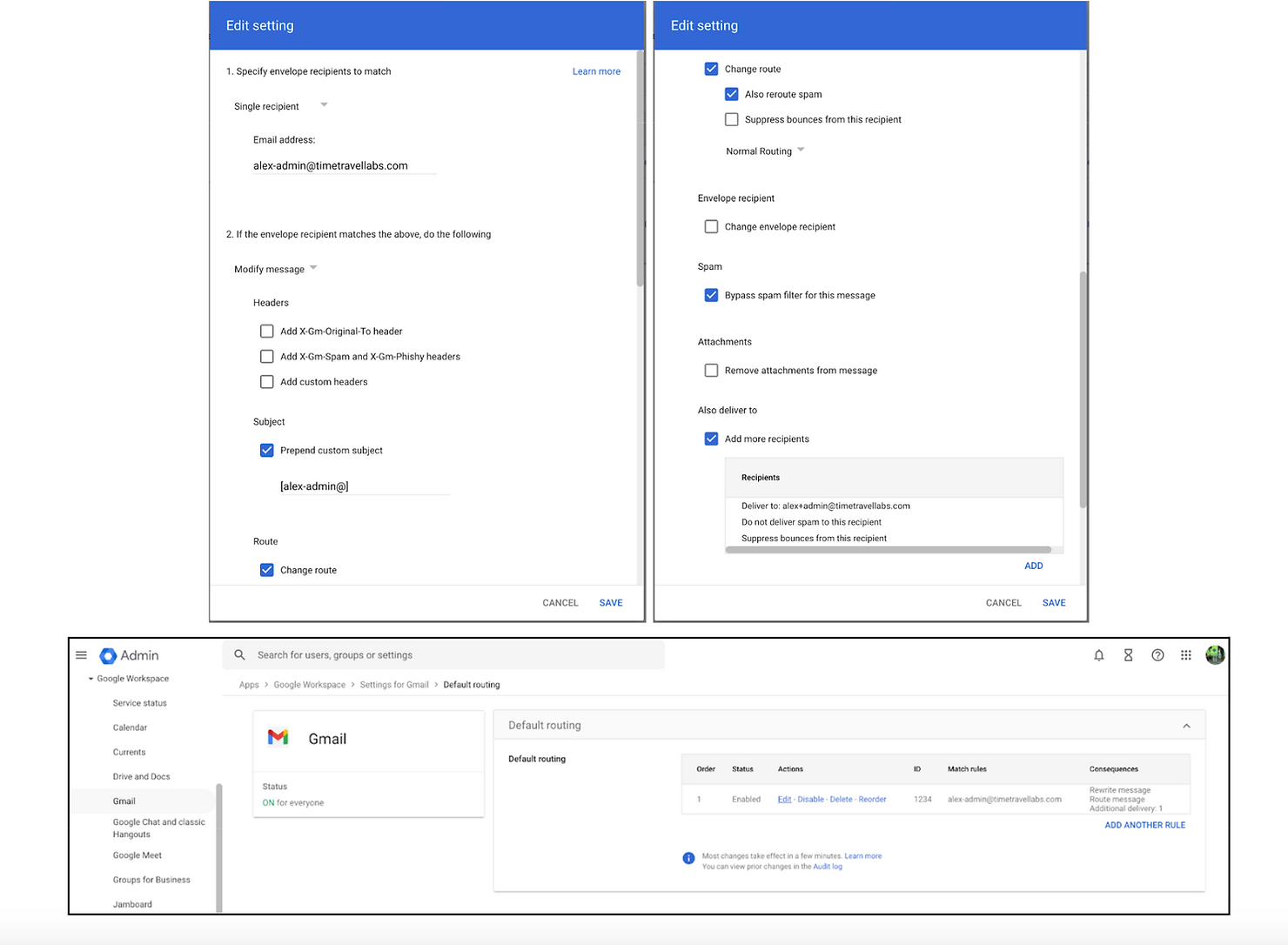
That’s it! You now have a free super admin account with no services attached to it and all emails are redirected to your user email.The neat thing about this technique is it’s great if you have a lot of contractors or other limited accounts that you need to bring on board.Want to save time onboarding employees, increase security, and save money? Try YeshID’s dead simple IAM, contact Dana or me.Want to build with us? Check out: https://www.yeshid.com/web-frontend-engineer.

